AWS ALB with AWS WAF to prevent DDoS attack

A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of Internet traffic. This is accomplished by using multiple compromised systems (often infected with malware) as sources of attack traffic. These compromised systems, which can include computers and other networked devices such as IoT devices, are often called bots, and collectively they form a botnet.
How a DDoS Attack Works:
- Attack Initiation: The attacker sends a command to the botnet, instructing all the bots to start sending requests or data to the targeted server.
- Overwhelming Traffic: The targeted server or network is bombarded with an overwhelming volume of traffic, which can exhaust its resources (like CPU, memory, or network bandwidth).
- Service Disruption: Due to the overwhelming traffic, legitimate users are unable to access the service, leading to a denial of service.
Types of DDoS Attacks:
- Volume-based Attacks: These attempt to consume the bandwidth of the target, overwhelming it with a high volume of traffic.
- Protocol Attacks: These exploit vulnerabilities in network protocols to consume resources on servers, load balancers, or other networking devices.
- Application Layer Attacks: These target specific applications to disrupt service by exhausting the resources at the application layer, like HTTP floods.
Importance of Preventing DDoS Attacks:
- Service Availability: DDoS attacks can take down a website or online service, rendering it unavailable to legitimate users. This can lead to loss of revenue, especially for e-commerce platforms, and damage to the brand’s reputation.
- Security Risks: While the primary goal of a DDoS attack is to disrupt service, it can also be used as a smokescreen for more sinister activities, such as data breaches or insertion of malware, as IT teams are busy dealing with the DDoS.
- Financial Costs: Beyond the immediate loss of business due to downtime, the costs associated with mitigating a DDoS attack and restoring services can be substantial.
- Reputation Damage: Consistent or prolonged unavailability of services can erode customer trust and lead to long-term reputational harm.
- Legal and Compliance Issues: In some industries, downtime can lead to regulatory fines or breaches of contractual obligations with customers.
Preventing DDoS Attacks:
Preventing DDoS attacks involves a combination of strategies, including:
- Using Anti-DDoS Services: Many cloud providers offer DDoS mitigation services that can detect and filter malicious traffic before it reaches the target.
- Scaling Infrastructure: Auto-scaling infrastructure can absorb more traffic and reduce the impact of a DDoS attack.
- Traffic Filtering: Implementing traffic filtering rules, like rate limiting, can help prevent a flood of requests from overwhelming servers.
- Regular Network Monitoring: Continuous monitoring of network traffic can help in the early detection of unusual traffic patterns, allowing for a quicker response.
- Redundancy and Load Balancing: Distributing traffic across multiple servers or data centers can help in managing and mitigating the impact of an attack.
Preventing DDoS attacks is crucial for maintaining the integrity, availability, and reliability of online services, which are essential for customer trust and business continuity.
In this article, we will demonstrate how to prevent DDoS attacks using AWS WAF, comprising a demo infrastructure built with AWS ALB and EC2.
Configure AWS ALB & EC2
First, we will create an EC2 instance and set up a docker container to run there with a very simple app from the docker hub named fast-app. Then, we will set up an ALB to connect to the instance and put a stress test on the application.
Step 1: EC2
Launch an EC2 from the AWS console. Select the AMI Ubuntu Server 24.04 , 64-bit (x86) as architecture, instance type of t2.micro which is free tier compatible. On the network settings part, check Allow HTTP traffic from the internet, Allow HTTPS traffic from the internet, and uncheck Allow SSH traffic from. On the advanced tab, put the below user script that will set up and run the desired dcoker image for us. Now, you can launch the instance.
#!/usr/bin/env bash
# Add Docker's official GPG key:
sudo apt update
sudo apt install ca-certificates curl -y
sudo install -m 0755 -d /etc/apt/keyrings
sudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg -o /etc/apt/keyrings/docker.asc
sudo chmod a+r /etc/apt/keyrings/docker.asc
# Add the repository to Apt sources:
echo \
"deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/ubuntu \
$(. /etc/os-release && echo "$VERSION_CODENAME") stable" | \
sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt update
sudo apt install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin -y
sudo service docker start
sudo docker run -d -p 80:8000 ahmadalsajid/fast-app






Wait for a couple of minutes and then we can check if the application is properly working or not
$ curl http://your_ec2_public_ip/
{"Hello":"World"} Perfect, the EC2 and app is up and running.
Step 2: AWS ALB
At this point, create a target group first. Go to EC2 > Target groups > Create target group, and choose Instances as the target type, put a target group name, Protocol: Port set to HTTP : 80, IPv4 as the IP address type. Keep the rest as it is, and create the target group.




Now, go to EC2 > Load balancers > Compare and select load balancer type, and select Application Load Balancer. Follow the below screenshots accordingly to create the ALB.






Your ALB is up. Give it a try
$ curl http://demo-load-balancer-944xxxx45.us-east-1.elb.amazonaws.com/
{"Hello":"World"} Now, we can put some load on the ALB.
$ docker run --rm -it ahmadalsajid/oha-docker -n 20000 -c 500 http://demo-load-balancer-944026445.us-east-1.elb.amazonaws.com/
Summary:
Success rate: 96.76%
Total: 27.4261 secs
Slowest: 15.2206 secs
Fastest: 0.2306 secs
Average: 0.4041 secs
Requests/sec: 729.2334
Total data: 321.27 KiB
Size/request: 17 B
Size/sec: 11.71 KiB
Response time histogram:
0.231 [1] |
1.730 [18912] |■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■
3.229 [258] |
4.728 [153] |
6.227 [18] |
7.726 [5] |
9.225 [1] |
10.724 [2] |
12.223 [1] |
13.722 [0] |
15.221 [1] |
Response time distribution:
10.00% in 0.2434 secs
25.00% in 0.2521 secs
50.00% in 0.2664 secs
75.00% in 0.2925 secs
90.00% in 0.7389 secs
95.00% in 1.0652 secs
99.00% in 2.9996 secs
99.90% in 5.1774 secs
99.99% in 10.8284 secs
Details (average, fastest, slowest):
DNS+dialup: 1.6596 secs, 0.2499 secs, 4.6200 secs
DNS-lookup: 0.0001 secs, 0.0000 secs, 0.0051 secs
Status code distribution:
[200] 19352 responses
Error distribution:
[648] timeoutSee, we are making 500 concurrent requests to the ALB, which somewhat represents DoS, and we can observe some timeout errors there.
Step 3: AWS WAF
AWS WAF (Web Application Firewall) is a cloud-based firewall service provided by Amazon Web Services (AWS) that helps protect web applications and APIs against common web exploits that could affect availability, compromise security, or consume excessive resources. AWS WAF allows users to create rules to filter specific types of traffic to their web applications based on various criteria, providing an additional layer of security.
Key Features of AWS WAF:
- Customizable Rules: Users can create custom rules to block or allow traffic based on specific patterns. This includes filtering based on IP addresses, HTTP headers, HTTP body, URI strings, SQL injection, and cross-site scripting (XSS) attacks.
- Pre-configured Managed Rules: AWS WAF provides managed rule groups that are regularly updated by AWS and AWS Marketplace security vendors. These rule groups can help protect against common threats like OWASP Top 10 vulnerabilities, bots, and bad traffic, without the need for users to manage the rules themselves.
- Rate Limiting: AWS WAF allows users to set rate-based rules to automatically block IP addresses that exceed a specified request threshold in a given time period. This feature is particularly useful for mitigating DDoS attacks.
- Real-time Visibility: AWS WAF integrates with AWS CloudWatch, providing real-time monitoring and logging of web traffic. Users can view detailed metrics and request data, enabling them to analyze patterns and adjust rules as necessary.
- Integration with AWS Services: AWS WAF integrates seamlessly with other AWS services, such as Amazon CloudFront (CDN), AWS Application Load Balancer (ALB), and AWS API Gateway. This integration allows for centralized management of security across different AWS services.
- Bot Control: AWS WAF provides a feature called Bot Control, which helps detect and manage automated bots that may be crawling your site or attempting malicious actions. You can set specific actions for known bots, such as blocking, allowing, or monitoring their activity.
- Protection Against Common Vulnerabilities:AWS WAF can protect against common web vulnerabilities, including SQL injection, XSS, and request forgery, through its rule sets. These rules can be tailored to address specific security needs.
- Geo-Blocking: Users can create rules that allow or block web requests based on the geographical location of the requests. This is useful for limiting access to certain regions or for complying with regional regulatory requirements.
- Automation and Infrastructure as Code: AWS WAF rules can be managed through AWS CloudFormation and other AWS DevOps tools, allowing for the automation and version control of security policies as part of the CI/CD pipeline.
- Cost-Effective: AWS WAF operates on a pay-as-you-go pricing model, where users only pay for what they use. This includes the number of rules deployed and the amount of web traffic inspected by the WAF.
- Security Automation: AWS provides security automation templates that can help users quickly deploy WAF configurations to mitigate specific threats, such as SQL injection and cross-site scripting, or to implement rate limiting.
Benefits of Using AWS WAF:
- Improved Security: Provides robust protection against a wide range of threats to ensure that web applications remain secure.
- Flexibility: Users can tailor the WAF to their specific needs with custom rules, rate limits, and geo-blocking.
- Scalability: AWS WAF scales automatically to handle large volumes of traffic, making it suitable for applications of any size.
- Ease of Use: With managed rules and seamless integration with AWS services, AWS WAF simplifies the deployment and management of web application security.
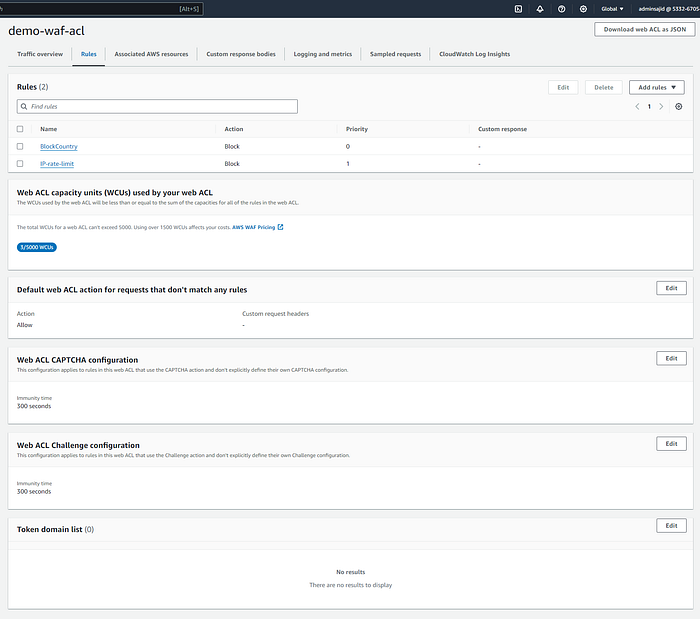
Let’s create a WAF and integrate with the previously created ALB
Go to AWS WAF > Web ACLs > Create web ACL and follow the steps below to create a custom rule that will prevent requests originating from some specific country, i.e. Japan, USA [or any other country that we can mimic with VPNs], use Add Rules > Add my own rules and rule groups









Our WAF ACL is configured. Now, let’s Start the VPN, fly to Japan, and try to curl to the ALB DNS we have from the Last steps.
$ curl http://demo-load-balancer-944026445.us-east-1.elb.amazonaws.com/
<html>
<head><title>403 Forbidden</title></head>
<body>
<center><h1>403 Forbidden</h1></center>
</body>
</html>Turn off the VPN, and try again
$ curl http://demo-load-balancer-944026445.us-east-1.elb.amazonaws.com/
{"Hello":"World"}Also, we can mitigate brute-force attacks by limiting the number of requests from a single IP address. We can add another rule to simulate a DDoS attack from a specific IP and block requests from that IP for a specified rate.



Now, let’s curl to the ALB first, and then put a stress test on it.
$ curl http://demo-load-balancer-944026445.us-east-1.elb.amazonaws.com/
{"Hello":"World"}
$ ab -n 20000 -c 500 -r http://demo-load-balancer-944026445.us-east-1.elb.amazonaws.com/
This is ApacheBench, Version 2.3 <$Revision: 1879490 $>
Copyright 1996 Adam Twiss, Zeus Technology Ltd, http://www.zeustech.net/
Licensed to The Apache Software Foundation, http://www.apache.org/
Benchmarking demo-load-balancer-944026445.us-east-1.elb.amazonaws.com (be patient)
Completed 2000 requests
Completed 4000 requests
Completed 6000 requests
Completed 8000 requests
Completed 10000 requests
Completed 12000 requests
Completed 14000 requests
Completed 16000 requests
Completed 18000 requests
Completed 20000 requests
Finished 20000 requests
Server Software: uvicorn
Server Hostname: demo-load-balancer-944026445.us-east-1.elb.amazonaws.com
Server Port: 80
Document Path: /
Document Length: 17 bytes
Concurrency Level: 500
Time taken for tests: 373.944 seconds
Complete requests: 20000
Failed requests: 20142
(Connect: 0, Receive: 598, Length: 18946, Exceptions: 598)
Non-2xx responses: 18196
Total transferred: 3535954 bytes
HTML transferred: 745758 bytes
Requests per second: 53.48 [#/sec] (mean)
Time per request: 9348.612 [ms] (mean)
Time per request: 18.697 [ms] (mean, across all concurrent requests)
Transfer rate: 9.23 [Kbytes/sec] received
Connection Times (ms)
min mean[+/-sd] median max
Connect: 0 1643 5085.9 540 66767
Processing: 239 6061 22708.9 548 288550
Waiting: 0 1754 4413.0 533 59774
Total: 483 7705 23131.9 1147 289385
Percentage of the requests served within a certain time (ms)
50% 1147
66% 2282
75% 3673
80% 4292
90% 9500
95% 33337
98% 131698
99% 133109
100% 289385 (longest request)You can see Non-2xx responses: 18196 out of 20000 requests. That means AWS WAF was blocking requests to prevent DDoS attacks.
